Información acerca de los productos
1 marzo, 2024 Software Vulnerabilities Notice Regarding Evident Microscope Software Due to a severe security vulnerability issue in a third-party component used in Evident Application Software, it is strongly advised to install the provided Service Update. This Service Update provides a version of the affected component that closes the vulnerability gap. The target software is as follows.
As a result of our survey, it revealed that there are two vulnerabilities.
CVE-2023-3935: A heap buffer overflow vulnerability in Wibu CodeMeter Runtime
Please see for more information.
Product Security Advisory WIBU-230704-01-v3.0
Product Security Advisory WIBU-231017-01
NIST(*1) NVD(*2) (*1) NIST: National Institute of Standards and Technology
The impact of the security vulnerability
CVE-2023-3935
a) CodeMeter Runtime (i.e., CodeMeter.exe) is configured as a server
b) CodeMeter Runtime is configured as a client
CVE-2023-38545
If you have installed the CodeMeter license server yourself, sending manipulated packets can cause a crash of it or possibly code can be smuggled in and executed. Workaround
Install the provided Service Update.
(For DP2-AOU users)
This service update is available for the following operating systems.
Confirmation before installationMake sure that all applications are closed. Installation Procedure1. Start Windows. 2. Log on with administrator rights.
3. Download the Service Update file (CodeMeter_7_60d.exe) from the below.
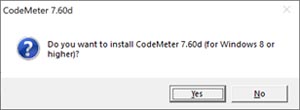
4. Make sure that all applications are closed. 5. Double-click the Service Update file. 6. If the user account control dialog is displayed, select 'Yes'. 7. When you are asked if you want to install CodeMeter 7.60d confirm with ‘Yes’.
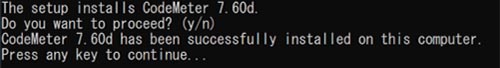
8. A console window appears, type ‘y’ to confirm and proceed.
9. When the setup is complete, press any key to close the console window.
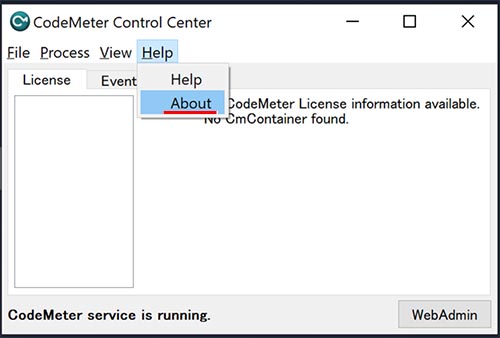
10. Check the version of CodeMeter.
(For DP2-AOU users)
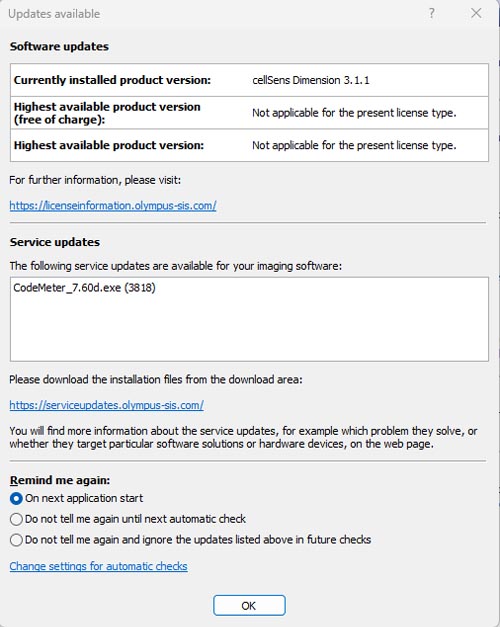
If you are using the cellSens or Stream, and have enabled the auto update function, please take the following actions. 1. If you are connected to the internet, it appears the update notice dialog on your PC when you start the software.
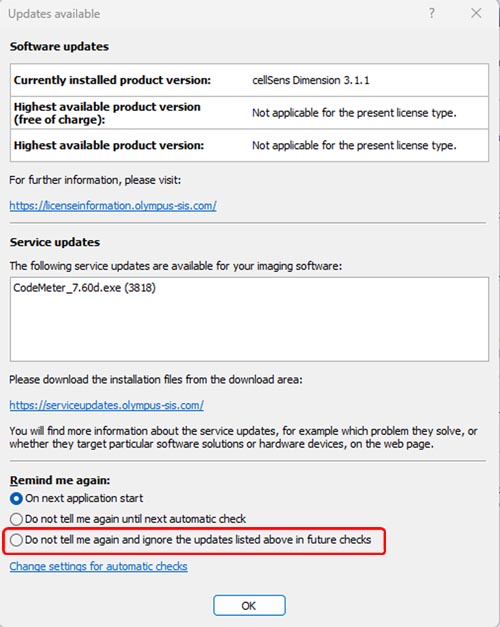
Select ‘Do not tell me again and ignore the updates listed above in future checks’ on Update notice dialog, then press ‘OK’.
2. If it appears the update notice dialog on your PC before updates, check the version of CodeMeter.
(a) The case that the version of CodeMeter is 7.60d.
(b) The case that the version of CodeMeter is NOT 7.60d.
|